In today’s digital world, securing your social media has never been more important. So, in honor of Cyber Security Awareness Month, here are 5 of our favorite social media security best practices that we think every individual and company should be using right now:
1. Check to see if you’re at risk.
Individuals, companies, and even governments have become increasingly reliant on haveibeenpwned.com, also known as HIBP. It’s an exceptionally good (and free!) web service that allows you to see whether your email address has been included in any major data breaches. If it has, assume that the password you used for that service is public knowledge—update all of your accounts that use it. Even if it hasn’t, it could be leaked in the future, so we highly recommend signing up for HIBP’s “notify me” service and also enabling multi-factor authentication through your email provider.
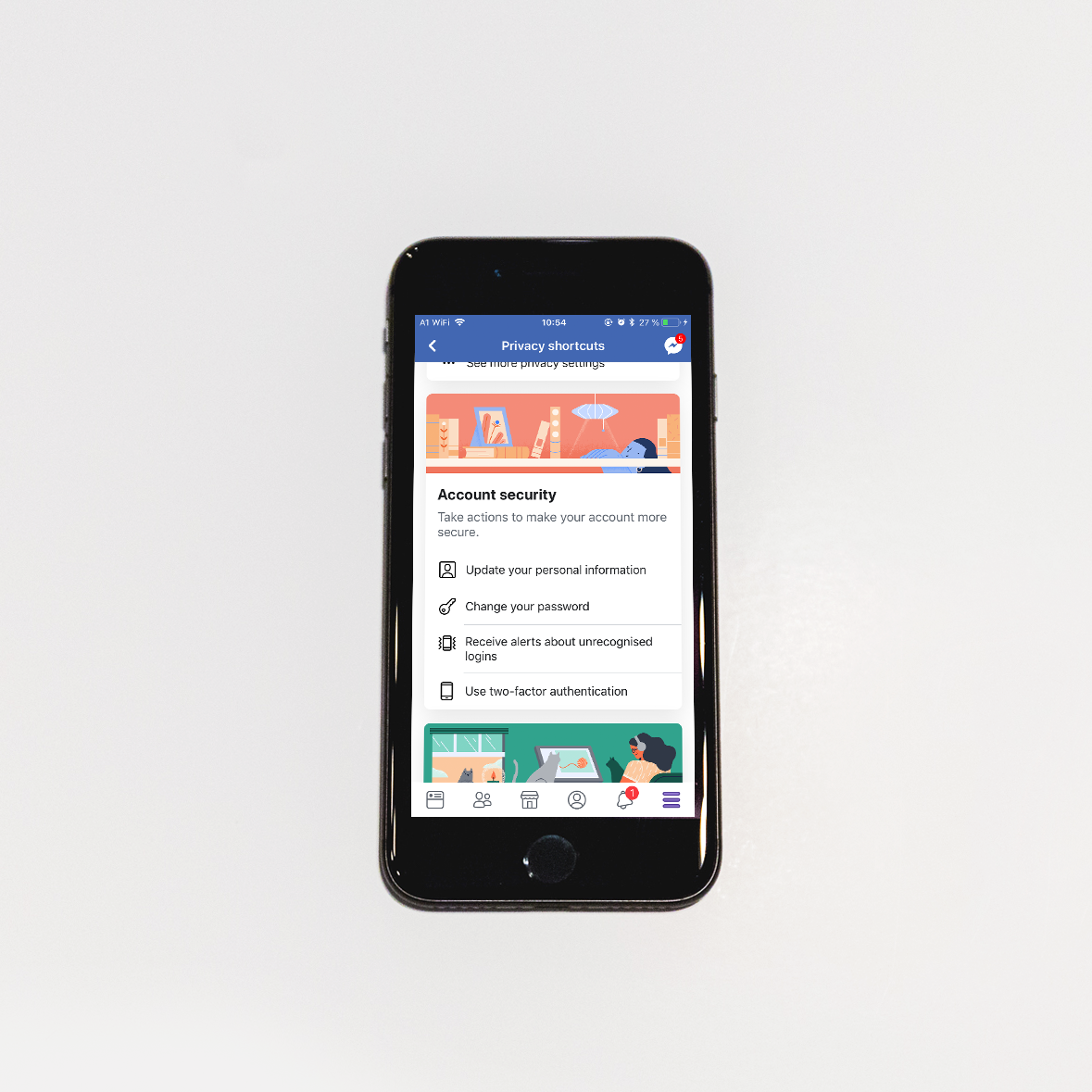
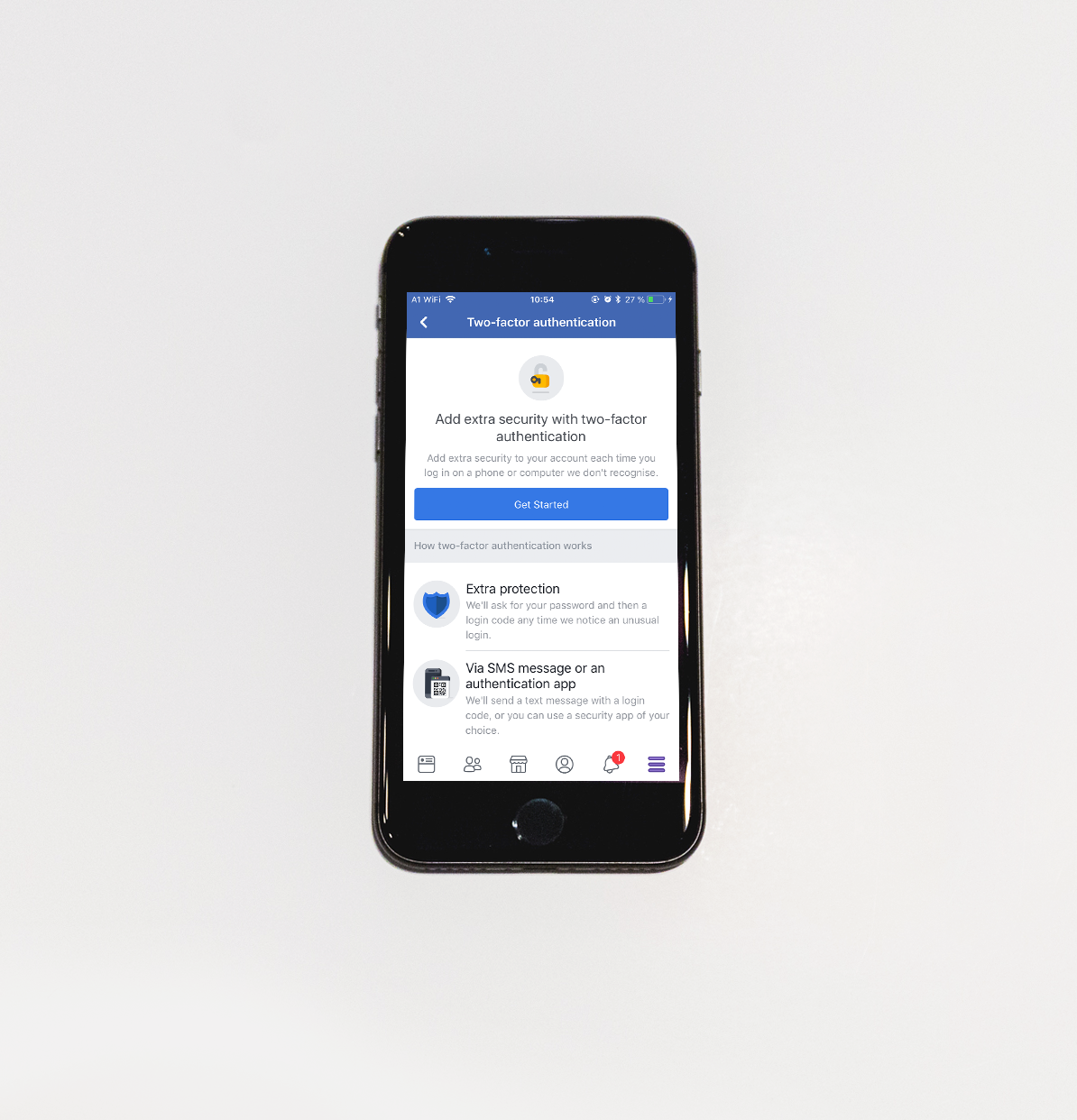
2. Use multi-factor authentication.
Many social media platforms have implemented multi- or two-factor authentication (MFA/2FA) as an added line of defense for their users. MFA, simply put, is when you use two or more different forms of identification to access your account. This strengthens the traditional username and password combo with a code that only a specific user has access to, like a smartphone. Here is where you can find 2FA
on Instagram:
on Facebook:
on Twitter:
Like we mentioned before, don’t forget to check whether your email provider supports two- or multi-factor authentication.
3. Revoke third-party access
With your permission, social media platforms allow third-party websites and apps to access different parts of your accounts. Have you ever logged into an app or site with Facebook? If so, then you’ve granted a third party permission to read and/or edit particular content on your personal or corporate account. Though this is standard practice, review the list of apps you’ve granted access to for each of your accounts and remove the ones you no longer use. On Facebook this can be found in the Authorization section of your page’s settings, and in the Apps and Websites section of your personal account’s settings. On Twitter, check the Apps and Devices section of your account settings.
4. Don’t login with Facebook
In addition to revoking already-existing third-party access, don’t use Facebook to log in to your other apps and sites. Though it’s very convenient to have a single login, it is less secure—especially considering the recent Facebook data breach. Though Facebook claims that attackers didn’t access any third-party apps during the breach, the mere possibility is troubling.
Farhad Manjoo, New York Times, describes why:
“This is a classic you-had-one-job situation. Like a trusty superintendent in a Brooklyn walk-up, Facebook offered to carry keys for every lock online. The arrangement was convenient — the super was always right there, at the push of a button. It was also more secure than creating and remembering dozens of passwords for different sites. Facebook had a financial and reputational incentive to hire the best security people to protect your keys; tons of small sites online don’t — and if they got hacked and if you reused your passwords elsewhere, you were hosed.
But the extensive hack vaporizes those arguments. If the entity with which you trusted your keys loses your keys, you take your keys elsewhere. And there are many more-secure and just-as-convenient ways to sign on to things online.”
Though this seems to imply that you need to remember individual logins (i.e. multiple passwords) for all of your sites and apps, it thankfully doesn’t. There are a lot of reliable password managers online that keep track for you; our favorites are Keeper and 1Password.
5. Create and maintain a social media security policy
Even though you’ve learned best practices for secure social media use, that doesn’t mean that your team has. Sit down and have a conversation with everyone that has access to your company’s social media accounts and define security standards.
Here are some initial questions to go over:
Who has access to which social accounts?
Are the emails associated with these accounts secure?
Has multi- or two-factor authentication been setup for the emails associated with these accounts, and for the social accounts themselves?
Which third-party apps have we granted access to?
Boom Creative Lab creates meaningful connections in a digital world; central to this, we are dedicated to maintaining the highest security standards for our clients. Interested in working with us? Check out some of our most exciting work, and connect with us today.